You are viewing our site as a Broker, Switch Your View:
Agent | Broker Reset Filters to Default Back to ListPreventing Real Estate Ransomware
July 25 2019
The real estate industry is increasingly aware of the dangers of ransomware, which have been raised due to some recent high-profile incidents. Ransomware is malware (malicious software) that encrypts the files on your network or otherwise blocks access to them. It's called ransomware because you may be prompted to pay a ransom to regain access to the files. Most security professionals advise clients to not pay the ransom because often the hacker will not unencrypt or allow access to the files as a result.
The purpose of this article is to suggest some best practices for avoiding ransomware, limiting its impact, and recovering from it. No suggested best practices can prevent all incidents of ransomware – there will always be a new attack that can bypass certain types of defenses. However, there are some reasonable steps you can take to reduce the ransomware risk for your organization.
Avoiding Ransomware
Most ransomware starts because an employee – or office visitor on your network – accesses a malicious website that spreads the virus to their computer. This often happens after they receive SPAM and click on the link, or they click on a website link – sometimes on a compromised trusted website – that leads to the virus.
Sometimes the malware is spread by a "drive-by-download" where a security flaw in a browser, browser plug-in, or e-mail client will automatically install the virus, even when the user has not clicked on a link or intentionally downloaded or installed anything. Less often, vulnerabilities in the local network or the operating system can be exploited to inject malware. Ransomware can also be installed from a USB memory stick when plugged into an organization's computer, with one study showing almost half of people will do just that when they find a memory stick on the ground.
Making sure your operating systems and installed software are kept "patched" with the latest security fixes is one of the most important things you can do to protect the organization. System administrators should use patch management software to ensure that all software is patched – especially but not limited to internet-facing software such as e-mail clients, web browsers, browser plugins such as Flash and Acrobat Reader. Network equipment, such as routers, firewalls, wireless access points, and so on, should also have the latest firmware installed.
On workstations, there are also advanced configurations to prevent ransomware. This may include software restriction policies to prevent end-users from accidentally installing malware, disabling macros in Microsoft Office, and reducing the risky behaviors possible within the web browser. To address this, some organizations remove administrative access rights from each user.
There are many antivirus solutions and endpoint protection platforms on the market, and they are not equally effective at detecting ransomware. There are many perspectives on these products. Regardless of which solution you choose, always ensure that the software is updated with the latest scan engine and malware/virus signature files.
Consider using your firewall's "web filtering" capability to limit access to only those websites needed for work (whitelist). If this is deemed too restrictive, then at least block websites with poor security reputations (blacklist).
E-mail servers and email firewalls can also be used to reduce SPAM that may include malicious links and strip away attached executable file types and files that may contain viruses or malware. Some email servers also allow you to add a warning to email coming from outside the organization to urge caution when interacting with the email.
Because phishing is such a common source of ransomware, an organization should train its employees to identify phishing emails and avoid opening or clicking on links from unknown or suspicious sources. There are various training and testing platforms that allow a company to send realistic (but harmless) phishing emails and view a report of which employees open them and click on links. Some platforms include e-learning content for those that click on the potentially harmful links. A well-designed program should eventually lead to fewer employees falling for phishing emails.
Limiting the Impact of Ransomware
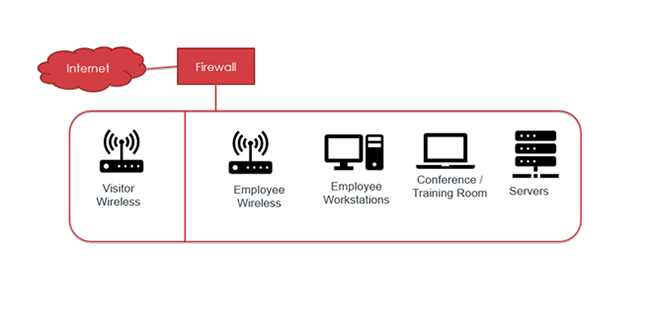
The most important thing a company can do to limit the spread of ransomware between computers on their network is to properly use a firewall. Many companies improperly use the firewall to protect their network only from the internet and not from threats that originate inside the firewall. For example, an employee may install ransomware on a workstation which quickly spreads to servers, or a visitor may bring malware with them into a conference room, allowing it to spread to employee workstations and servers. The image below shows a network that, once breached, will allow the ransomware to spread without ever alerting the firewall or its intrusion detection systems:
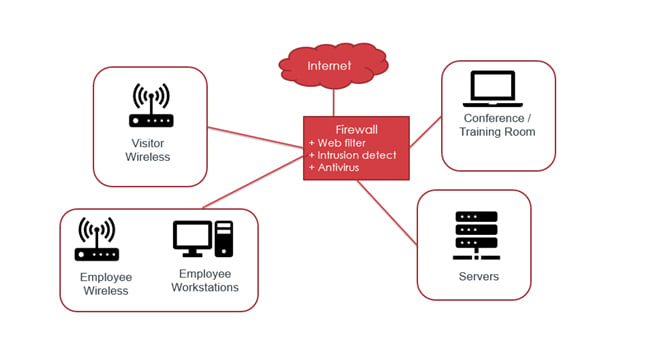
A well-designed network will use the firewall to only allow limited, mission-critical network traffic between areas of different security sensitivity, and the firewall systems may be able to detect when malware tries to move from computer to computer through it. For example, in the network pictured below, when someone brings an infected computer into the training room, the ransomware can be limited by the firewall so it doesn't have access to any other part of the network.
Once ransomware is inside the network, anything the downloading user has access to can be infected. That means, if the user's computer is connected to a file-server – or could be connected using the user's login credentials – that file-server can become infected. Likewise, if the user's credentials can be used to telnet, FTP, or use Remote Desktop to access other computers, that computer may be compromised. Advanced ransomware may also leverage other hacking tools to attack other computer weaknesses and attempt to collect other login credentials.
While file-shares and credentials-in-common are convenient, they make it easy for the ransomware to spread. If the company is willing to bear at least some inconvenience, these connections should be eliminated, and employees should use different credentials to access web-based file services.
Likewise, many executives, employees, and technical staff may be using "administrator" level computer and network logins on a regular basis, even when engaged in risky activities like browsing the web or reading email. Using the least-privileged account possible is ideal, with the "administrator" accounts being used only to administer the computer or network.
Recovering from Ransomware
As part of a larger incident response and business resumption plan, the company should identify local computer forensics and incident response specialists to contact in the event of a ransomware or other hacking incident. Having more than one contact handy is a good idea, in case a particular contact is otherwise engaged when you call. Store this information in a safe place – not just on your workstation, which may not be accessible.
Your most important tool for recovering from ransomware is having well-tested, multi-generational backups. Multi-generational means you can restore your files to how they were earlier today, yesterday, last week, or last month: you are not constantly overwriting your only backup with changed files from your network, and you have no "write" access to the older backups from your computer. Without multi-generational backup, the ransomware-encrypted files will overwrite your backup and you can't restore to anything earlier. Testing the backup is important to ensure you have everything you need for recovery. What if you must completely re-format your computers, go back to an old virtual image, or even buy new computers? How quickly can you recover? If you have never tested your backup and recovery process, you don't know.
Final Words
This article should provide a starting point for executives and their technical staff for avoiding ransomware, limiting its impact, and recovering from it. There is no such thing as "secure," only choices that companies can make to reduce risk, including but not limited to extensive training and test phishing campaigns, the removal of administrative access, advanced filtering of websites that employees visit, disabling of USB key access and CD/DVD drives, and much more. It is imperative that our industry choose to continue to improve security practices and to protect the infrastructure that supports our critical industry.
To view the original article, visit the CoreLogic blog.