You are viewing our site as an Agent, Switch Your View:
Agent | Broker Reset Filters to Default Back to ListNot All eSignature Platforms are Created Equal
April 10 2014
There's been a lot of talk lately about the security of electronic signatures and the legal havoc that using the wrong solution could wreak on your business. That's why we took careful notes when our sister company, the WAV Group, hosted a webinar on this topic last Thursday.
Tom Gonser, CEO of DocuSign, Ken Moyle, DocuSign's Chief Legal Officer, Martin Scrocchi, CEO of Instanet Solutions, and Russ Bergeron, President of MRED joined moderator Marilyn Wilson to help webinar attendees:
- Learn how to ensure that electronic signature solutions are legally viable
- Better understand how to evaluate electronic signature platforms
Couldn't attend the event? No worries! You can watch the full recording below or read our summary on the next page.
Legal contracts are a critical part of real estate. Real estate professionals need to be sure they're providing tools to customers that protect their clients' interests and well as their own.
It's not always easy to sort out what those tools are, however. A simple search for "electronic signatures" on the App Store or Google Play will yield dozens of results. How can you know which solutions to trust and which to avoid? Knowing what questions to ask and what elements are most important in an eSignature solution is a great place to start.
From a legal standpoint, the following two items are most important:
- Identification - How do you match the person with the signature?
- Authentication - Once a document is signed, can you demonstrate that it hasn't been tampered with?
We can look to banks to find out more about how to evaluate solutions. Many larger banks now provide requirements or recommendations on the type of support electronic signatures must have to be legally viable within their programs. They want to be able to see the entire "story" of a document--where it's been, who's signed it, and more. This can be accomplished via a certificate of completion, a transaction summary that demonstrates authentication procedures, timestamping, audit trail and more. All of these are evidentiary bits that support the integrity of the transaction in case it is ever challenged.
When researching solutions, if a company's website or other literature doesn't satisfactorily address authentication and data integrity, keep looking. You can run into trouble later if you don't choose wisely.
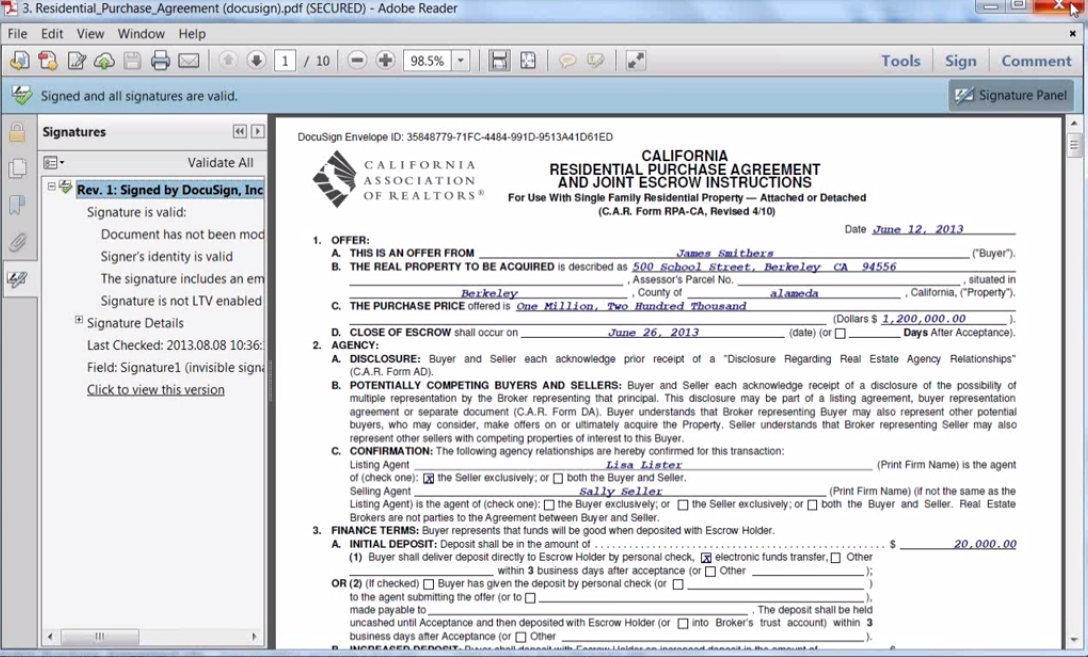
What Does a Trustworthy Document Look Like?
The webinar concluded with a demonstration of what a trustworthy document looks like. Anytime a document is opened, it's checked for validity. A trustworthy document, like the one below, will be verified as having all signatures valid.
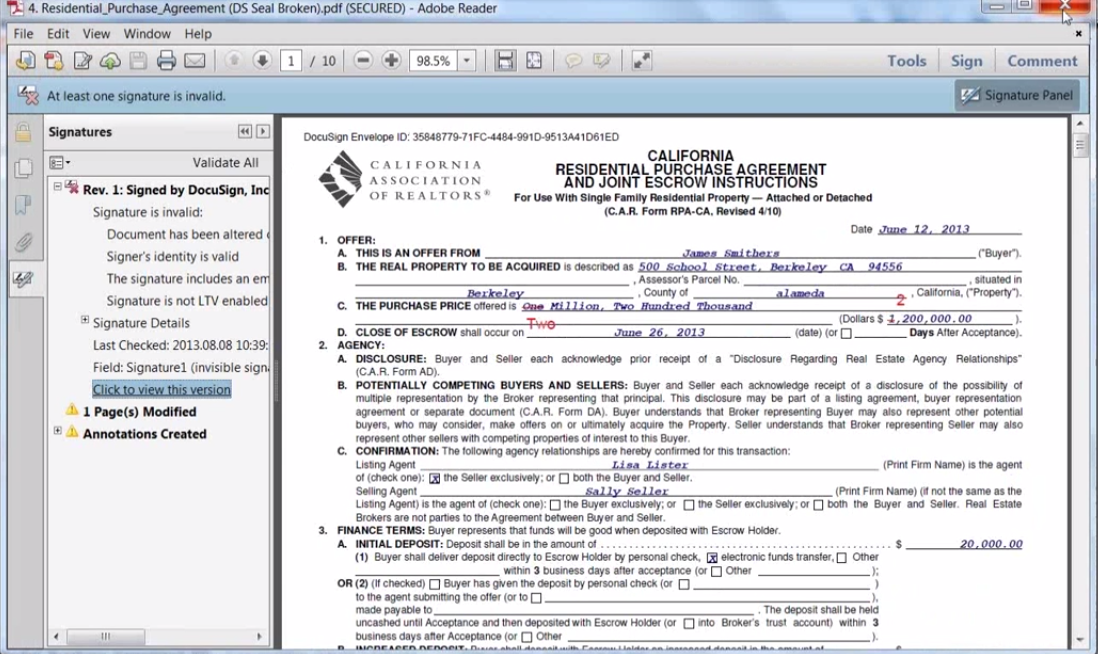
This document, however, has been tampered with, as evidenced by the message near the top of the screen. The sidebar also shows what parts of the document have been changed.
Ready to learn more? These were just a brief overview of points from the webinar. View our recording on page one to listen to advice from our guest experts.