You are viewing our site as an Agent, Switch Your View:
Agent | Broker Reset Filters to Default Back to ListCRYPTO – Ransomware at its Deadliest
June 30 2014
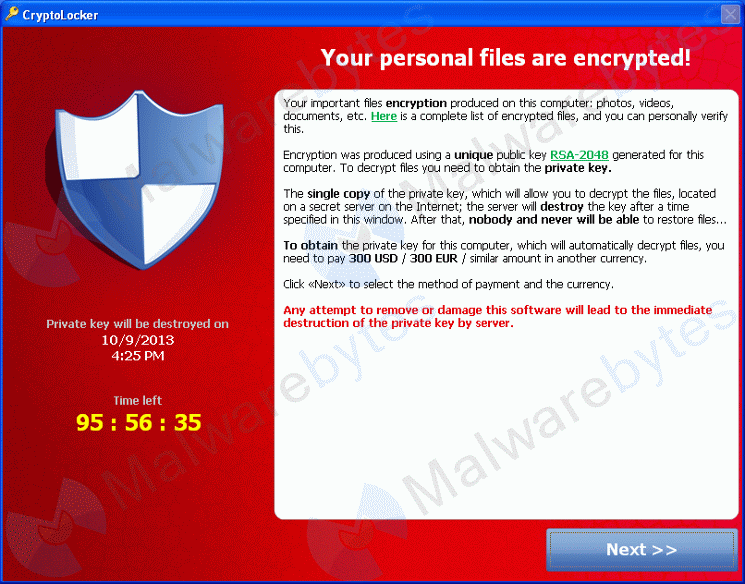 Have you heard of ransomware trojans? These are viruses that lock down your files and your computer and ask you for payment to restore your access to them.
Have you heard of ransomware trojans? These are viruses that lock down your files and your computer and ask you for payment to restore your access to them.
Some well-known ransomeware trojans are CyrptoLocker, CryptoWall, CryptoDefense and CryptoBit – all these come from the same developer. These are not your average malware that can be removed with a scan. These are nasty, advanced ransomware that affect your computer in a way from which you cannot recover. Using a 2048-bit RSA encryption, it locks as many files as it can before you even know it is on your computer. Then, it asks you for payment to recover them. Payment demands can range between $300 to $2,300.Choosing to pay or not pay the ransom is your decision; nevertheless, I do not recommend it.
This complex Trojan is notorious when it comes to locking down your files, as well as your ability to access it. To give you an example of how potent this is, it uses a DNS Sink Hole to cover its tracks; it redirects any possible way of routing to the source and throws it into limbo. You could lose all your files permanently – even if you pay the ransom.
Here is some advice.
PREVENTION:
- Constantly back up all your files in an external hard drive or a cloud program.
- Never open emails with attachments from unrecognized senders.
- Be careful what you download from websites unless they are from a legitimate source.
IF YOU HAVE BEEN INFECTED (and you choose not to pay the ransom):
- The first thing you want to do is turn the computer off and start it up in safe-mode with networking.
- To start safe mode: turn the computer on and start tapping the F8 key until you have the option to select safe mode with networking (This mode opens only the essentials, which shouldn't include cryptolocker.)
- From there, run the program named ListCrilock.exe Backup anything new worth backing up in a different external drive and turn the computer off.
- This program will list all your files that the virus has already encrypted.
- Have a local tech clear any CryptoLocker remnants. I personally advise a wipe and reload of the computer; I would not risk there being one piece of that virus left on my computer.
WHAT NOT TO DO:
Unless it is in SafeMode:
- Do not plug in anything such as a USB Drive, Camera, SD Card.
- Do not connect to a network drive; it will encrypt anything there, too.
- Do not panic; be sure to contact a local tech immediately.
To view the original article, visit the Tech Helpline blog.